The only thing I remembered about emulating Mifare Classic on Android is this Sackoverflow post: I wish you the best for your work. You have to succeed in Mifare Classic Emulation for Android. I want to use it Kind regards Ikarus. Yes ofcourse, this is the whole reason I spent my scholarship stipend money on a PM3 board.
- MiLazyCracker Hack Mifare 1K Classic. Juni 6, 2020 / IT Security / 2 Kommentare. Find out the Keys of a NFC Chip with miLazyCracker, Dump the Card with the hacked keys, Clone the dump onto a second card, Check if the contents are the same and change the manufacture block 0 with some china cards (mfcuk and mfoc command).
- MD4/MD5/NTLM1 hash cracker: medusa: 2.2: Speedy, massively parallel and modular login brute-forcer for network: mfoc: 0.10.7+38+gba072f1: MiFare Classic Universal toolKit: mkbrutus: 27.ddd5f8e: Password bruteforcer for MikroTik devices or boxes running RouterOS.
MIFARE® 1K Classic Key Fobs - USA Supplie
- It allows to recover authentication keys from MIFARE Classic card. Project on Github. https://github.com/nfc-tools/mfoc. Build from Source autoreconf -is ./configure make && sudo make install Usage Help Usage: mfoc [-h] [-k key] [-f file] [-P probnum] [-T tolerance] [-O output] h print this help and exit k try the specified key in addition to the default keys f parses a file of keys to add in addition to the default keys P number of probes per sector, instead of default of 20 T nonce.
- MIFARE CLASSIC 1K/4K USER MANUAL, Release 1.1.0 • MIFARE® Classic EV1 4K (MF1 S70) - Available as 4-byte NUID or 7-byte UID -4K EEPROM Size (32 sectors with 4 blocks and 8 sectors with 16 blocks) - Supports credit/value operations i.e. Increment/Decrement 32-bit Signed Integer value - Anti-collision suppor
- The regular procedure to use MIFARE cards is, to personalize the blank card with customer data and initialize the keys. Initialize the key means to overwrite the factory-set default keys with keys created in your office e.g.: from a random number generator. After this personalizing you hand-out the card to the end user
- The first block of the first sector of an original MIFARE Classic tag is read-only i.e. not writable. But there are special MIFARE Classic tags that support writing to the manufacturer block with a simple write command (often called magic tag gen2 or CUID). This App is able to write to such tags and can therefore create fully correct clones. FUID and UFUID tags should work too, but they have not been tested so far. However, the app will not work with all special tags. Some of them.
I know using mifare classic is not as secure as mifare desfire, but I don't have enough knowledge with desfire neither mifare plus yet so I'll start with classic first. I would like to implement mifare classic in a door lock, but I don't know how. Let's just say I will use the sector 4. Then I'll change the authentication key. Then what's next? Is this all I need to do? Or should I write. Mifare Classic Tool Modded app by NokisDemox. This is an educational video showing you some more features for mct app and how nfc tags are vulnerable.Follow. Mifare hack read IC Card with MTools and Mifare classic tools without acr122u - YouTube. New Design RFID-PN532: https://shop.mtoolstec.com0:00 Quick look on the phone and card for testing.0:30. But there are special MIFARE Classic tags that support writing to the manufacturer block with a simple write command. This App is able to write to such tags and can therefore create fully correct clones. However, some special tags require a special command sequence to put them into the state where writing to the manufacturer block is possible RFIDDiscover - NXP's 13,56 MHz contactless IC products expert tool. NFC TagInfo App by NXP, available in the Google Play Store, helps you to check which MIFARE product is in a card. NFC TagWriter App by NXP stores contacts, bookmarks, SMS, Mail, text messages and many more to any NFC-enabled tag
How to use Mifare Classic Offline Cracker - MTool
- About MIFARE Classic Tool • Read MIFARE Classic tags • Save and edit the tag data you read • Write to MIFARE Classic tags (block-wise) • Clone MIFARE Classic tags (Write dump of a tag to another tag; write 'dump-wise') • Key management based on dictionary-attack (Write the keys you know in a file.
- How to copy MIFARE® Classic Sectors - YouTube. Tutorial:Easy copy MIFARE® Classic sectors.http://www.mpsys.de. Tutorial:Easy copy MIFARE® Classic sectors.http://www.mpsys.de.
- Just bring an Android phone with the Mifare Classic Tool on it, add your new found keys to their key file and read it: Mifare Classic Tool: dump of the card There you have it
Crack Mifare card key using brute-force attack with NFC smartphone and Mifare Classic Tool (Modified) - YouTube. Crack Mifare card key using brute-force attack with NFC smartphone and Mifare. All client applications (activities) using the library need to provide an implementation of the following interface: public interface MifareClassicDataInterface { void RegisterNewIntent(Intent mfcIntent); Context GetApplicationContext(); Activity GetApplicationActivity(); void PostTagScanKeyMapProgress(int position, int total); void PostTagScanSectorReadProgress(int position, int total); https://play.google.com/store/apps/details?id=tk.toolkeys.mtoolsHow to: https://why.yuyeye.cc/post/mtools-guideThis is the latest feature of NFC MTools, whic..
To read and write, the nfc-mfclassic tool is used. This tool was mainly developed for security research purposes on these cards, so it is not extremely simple and useful for conventional use. Indeed, it does not allow to directly indicate the sector that one wishes to read and the key to use. Instead, it proposes to the user to pass as argument a file containing a dump (with the keys included. This is a low-level tool for reading, writing and analyzing MIFARE® Classic RFID tags. It is designed for users who have at least basic familiarity with the MIFARE® Classic technology. It provides several features to interact with (and only with) MIFARE® Classic RFID-Tags. GENERAL INFORMATION This tool provides several features to interact with (and only with) MIFARE Classic RFID-Tags. It is designed for users who have at least basic familiarity with the MIFARE Classic technology. Please. MIFARE Classic Tool. This is a low-level tool for reading, writing and analyzing MIFARE® Classic RFID tags. It is designed for users who have at least basic familiarity with the MIFARE® Classic technology. It provides several features to interact with (and only with) MIFARE® Classic RFID-Tags
Basic Tutorial for MIFARE Classic 1K using C#, C++ etc
- RFID / NFC :: Mifare Classic 1k info and tools. Awesome Open Source. Awesome Open Source. Mifare Classic Toolkit. RFID / NFC :: Mifare Classic 1k info and tools. Stars. 47. License. gpl-3.0. Open Issues . 5. Most Recent Commit. 5 years ago. Related Projects. arduino (727)card (88)nfc (48)rfc (22)rfid (16) Repo. RFID-toolkit. Set of tools needed to interact with RFID tags over arduino. Basic.
- This is a list of Android devices which are complatible to MIFAREClassicTool. This app has been known to work on the following devices because their hardware (NFC-controller) does support MIFAREClassic . Asus Pegasus 2 (X550) BQ Aquaris X2 Pro; BQ Aquaris X5 Plus (Android 7.1.1) Google Nexus 7 (2012) Google Nexus 6P; Google Pixel; Google Pixel
- Is it possible to use a MIFARE Classic chip with sector coding, and simultaneous support NFC. Map the MFClassic sector to NFC, read from all NFC compatible mobile phones. So, read out the sector from the Mifare Classic chip on a regular Mifare reader and at the same time an NFC mobile phone? Br Svee
- Here you can find the changelog of Mifare Classic Tool since it was posted on our website on 2021-02-22 11:34:44. The latest version is 0.1 and it was updated on 2021-04-21 14:53:04
- Cloning a MIFARE Classic 1k Mathieu Bridon https://mathieu.daitauha.fr; You will need writable NFC tags, compatible with MIFARE Classic 1k. Make sure their sector 0 is writable. I used those (just the tags). 1. Try dumping the tag. Place the original on the reader, then try dumping it:
- • Write the manufacturer block of special MIFARE Classic tags • Create, edit and save key files (dictionaries) • Decode & Encode MIFARE Classic Value Blocks • Decode & Encode MIFARE Classic Access Conditions • Compare dumps (Diff Tool) • Display generic tag information • Display the tag data as highlighted hex • Display the tag data as 7-Bit US-ASCI
MIFARE Classic Tool. 使用 Google 翻譯將說明譯成繁體中文?. This is a low-level tool for reading, writing and analyzing MIFARE® Classic RFID tags. It is designed for users who have at least basic familiarity with the MIFARE® Classic technology. It provides several features to interact with (and only with) MIFARE® Classic RFID-Tags Mifare Classic Tool Key Driver Interface You; Mifare Classic Tool Key How To I Write; For a MlFARE Classic 1K you have 16 sectors with 4 blocks for each sector. For writing á Key A l use; cCard.IoadKey(aKey, eKeyStore); éKeyStore 0; aKey6 FF,FF,FF,FF,FF,FF My access bits KeyA is in Sector 1 Block 3
. It is designed for users who have at least basic familiarity with the MIFARE® Classic technology. It provides several features to interact with (and only with) MIFARE® Classic RFID-Tags. GENERAL INFORMATION This tool provides several features to interact with (and only with) MIFARE Classic RFID-Tags MIFARE Classic ones especially, which are still widely used nowadays despite the many hacks found throughout the last few years. This is not intended to teach you all about RFID, NFC, and MIFARE hacking. So, before we jump in let's learn some basics. RFID, NFC & MIFARE : The Basics. Radio Frequency Identification (RFID), is a technology that uses electromagnetic fields to automatically. Mifare Classic - intro, hardware needed Card UID, cloning access control badge using phone Mifare Classic data Attacks and required hardware - brute leaked keys, clone hotel key - nested, darkside, hardnested attack But I really need to be able to format cards to NDEF, and to read and write NDEF data on a MIFARE Classic 1K card. Does anyone know how to do so? Is it possible to use the libnfc.dll to do so? Does anyone have exemple or tutorial on this? For security matters, is it better to have DESFire 4k or 8k instead of MIFARE Classic 1k in order to be sure that my card is secure (can not be overwritten.
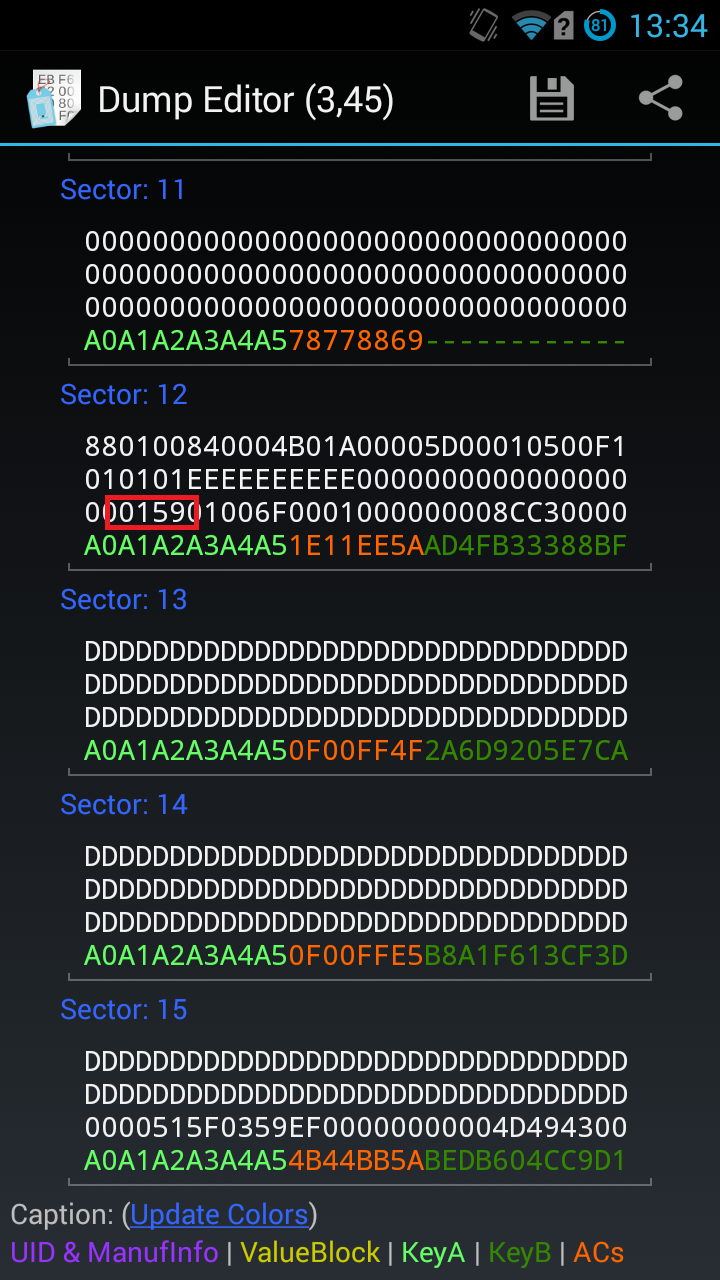
Some cards using default keys like FFFFFFFFFFFF 000000000000 A1B2C3D4E56F etc, which you can try to dump keys with Mifare Classic Tools on the NFC android phone. If the card is not full encrypted, it can be cracked with RFID device to burst crack. Like ACR122U or PN532. If the card is full encrypted, only PM3 can crack the keys. Compare to find the sector with money data. With keyA or keyB of. MIFARE Classic Tool Read MIFARE Classic tags Save, edit and share the tag data you read Write to MIFARE Classic tags (block-wise) Clone MIFARE Classic tags (Write dump of a tag to another tag; write 'dump-wise') Key management based on dictionary-attack (Write the keys you know in a file. Make social videos in an instant: use custom templates to tell the right story for your business. Live Streaming. Broadcast your events with reliable, high-quality live streaming. Screen Recorder. Record and instantly share video messages from your browser. Enterprise. Get your team aligned with all the tools you need on one secure, reliable. Use an applet that speaks APDUs on the one side and accesses the MIFARE Classic memory area 1 on the other side. NXP provides a ready-made applet for this that may or may not be enabled for the contactless interface. Also NXP provides an API that you could use within your own applet 2 to access the MIFARE Classic memory area 1
But there are special MIFARE Classic tags that support writing to the manufacturer block with a simple write command (often called magic tag gen2 or CUID). This App is able to write to such tags and can therefore create fully correct clones. FUID and UFUID tags should work too, but they have not been tested so far. However, the app will not work with all special tags. Some of them require how to use mfcuk (Page 1) — NXP MIFARE Classic — nfc-tools developers community — Public platform independent Near Field Communication (NFC) librar MIFARE Classic? MIFARE Ultralight? Reading and capturing contents of the card; About this manufacturer block (Sector 0 - Block 0) The UID thing that messes with my head; Writing a 4Byte dump on a different card; Why? The MIFARE NFC card is used in many environments. I got a trash card, a card that I have to use to open the underground trash bin, that I want to clone. As the replacement costs. . Reading the UID. The steps required in reading the UID from a contactless card requires the following steps. 1. Get context handle (SCardEstablishContext) 2. Connect to the card on the reader (SCardConnect) 3. Send the Get Data Command using SCardTransmit. (See section 3.3.5.1.3 in Part 3 of the PC/SC specification for more.
MIFARE Classic Tool (MCT) - GitHu
- MAD version 1 and 2 are used with MIFARE Classic cards. MAD version 1 uses sector 0 of the card to assign the remaining sectors (sectors 1..15) to specific applications (each sector can be assigned to one application ID indicating the application that manages/uses those sectors). MAD version 2 is an extension of MAD v1 that is used with MIFARE Classic 4K cards. MAD version two uses sector 16 as an additional directory to assign the 4K-specific sectors (sector 17..39) to applications
- In summary, I was able to successfully emulate a mifare classic chip (our id card) and gain access to all facilities as if I was using my id card (lenel access control). However, in the end the solution was a hack and a half. Only devices with NXP NFC controllers could this be possible on. Further, I had to modify the nfc_access.xml (remount the file system to rw) system file and include the signature of the application. Then using reflection, enable mifare emulation. Then using a mifare.
- Free Money - Just use your mobile... (MiFare Classic Hacking) Published on October 19, 2016 October 19, 2016 • 12 Likes • 0 Comment
- This is a low-level tool for reading, writing and analyzing MIFARE Classic RFID tags. It is designed for users who have at least basic familiarity with the MIFARE Classic technology. It provides several features to interact with (and only with) MIFARE Classic RFID-Tags. Read MIFARE Classic tags. Save, edit and share the tag data you read
- The easiest way to clone Mifare NFC Classic 1K Cards is by using an Android smartphone with NFC capabilities. That's right, your cellphone can be used to compromise the security of a company if they are using these types of cards (RFID security system). Just download the Mifare Classic Tool for Android
rfid - How to use mifare classic as a key? - Stack Overflo
Et bien dans la section Tools de l'application Mifare Classic Tool, vous pourrez trouver un utilitaire appelé Diff Tool qui vous permettra de comparer les deux sauvegardes/dumps comme vous le voyez ci-dessous. Secteur par secteur, l'application vous montre si la copie et l'original sont identiques. Voici la liste des outils disponibles dans l'application MCT pour manipuler les dumps. You can implement AN11028-style MIFARE Classic key diversification with the changes in #79, by using mifare_key_deriver_end_raw () to get the raw output bytes from an AES128 diversification operation. It is straightforward enough that it might even warrant closing this bug once #79 gets merged. Copy link [+] Chunk: 3.2s | found 30/32 keys (24) [+] Time to check 23 known keys: 3 seconds [+] enter nested attack [-] Tag isn't vulnerable to Nested Attack (PRNG is not predictable). #which is why we. ATQA 00, 04 is listed in ISO/IEC 14443 Type A generations and is identified as MIFARE Classic. Goody! It's weak and hackable. Just running mfoc to see if a slow attack can proceed: # mfoc -O card.dmp Found Mifare Classic 1k tag ISO/IEC 14443A (106 kbps) target: ATQA (SENS_RES): 00 04 UID size: single bit frame anticollision supporte Now I want to change them to something else. I'm using APDU structure. I'm sending commands like this and it works well: byte [] baData = { 0x01, 0x00, (byte)i, 0x60, 0x00 }; APDUCommand apdux3 = new APDUCommand ( (byte)0xFF, (byte)0x86, (byte)0x00, (byte)0x00, baData, 0x05); It works well
Mifare Classic Tool Bruteforce Mod V3
- In this case it's a Mifare 1k card. This also shows us the UID (ba2ea6ab) of the card, which we'll need later. From there we can find keys in use by checking against a list of default keys (hopefully one of these has been used): proxmark3> hf mf chk * ? This should show us the key we require looking something like
- SMRFID Mifare v1.2 (for Windows) Software tool designed for configuring, evaluating and testing Mifare Readers and modules. For new features of 2nd Generation modules (SM521X) and readers please use the newest tool Mifare Panel above. Windows (old) SBoot Upgrader v1.2 (for Windows) Firmware upgrade tool for windows (.NET). Requires encrypted .xml file to upgrade
- I use a Raspberry Pi with a reader connected by SPI) reader, and even longer with Mifare Classic Tool. You can then use the above tools to make a dump of the tag, providing you obtain the key. If there is only data stored in the top row of sector 0 (not including the bottom row), this means the readers only look at the ID of the card. If your phone is rooted, you can then use this app to.
- Mifare classic data structure Sector = 4 blocks of 16 bytes. Last block of a sector: •2 different keys (e.g. for separate read/write) •access rights for the keys Block 0 -READ ONLY UID Block 1 Block 2 KeyA | access rights | KeyB Block 4 Block 5 Block 6 KeyA | access rights | KeyB Sector 0 Sector
- Using widely available tools, the attacker cracked the card's authentication key. With the cracked key and the native NFC support in Android and the device, cloning a card and adding credits can be easily implemented in a mobile app. Figure 3. Manufacturer and memory content of a MIFARE Classic card. Attacks on other kinds of MIFARE cards (specifically, MIFARE DESFire and MIFARE Ultralight.
- Mifare Classic cards have either 1K or 4K of EEPROM memory. Each memory block can be configured with different access conditions, with two seperate authentication keys present in each block. Mifare Classic cards are divided into section called sectors and blocks. Each sector has individual access rights, and contains a fixed number of blocks that are controlled by these access rights. Each block contains 16 bytes, and sectors contains either 4 blocks (1K/4K cards) for a total.
Mifare hack read IC Card with MTools and Mifare classic
- MiFare card is need to be put close to or simply on the top of the MiFare reader/writer CR038, before executing the Mode 2, 3, 4 and 5. *Regarding the interfacing circuit, Button 1 is used to select which mode is going to be executed while Button 2 is used to execute the mode selected. *The BBFUINO board need to be reset each time the user select different modes for execution
- Whilst generally it is best practice to use unique Mifare Classic 14443A cards for each user, there are some instances where you may wish to clone a card and have multiple cards with the same UID and data. For example access control with few users with no user having the ability to add new cards into the system
- Authentication with Mifare Classic using libnfc (Page 1) — NXP MIFARE Classic — nfc-tools developers community — Public platform independent Near Field Communication (NFC) librar
- Ah, I guess the card will response with NAK 0x04 (Invalid operation, transfer buffer invalid) to the Transfer command if the previous increment/decrement/restore command was not successful. Then everything would make sense
- Mifare Classic Tool 4.0.1 by IKARUS Projects. Publication date 2020 Topics NFC, RFID, f-droid apk Language Multiple. An NFC app for reading, writing, analyzing, etc. MIFARE Classic RFID tags. New in version 4.0.1 * Improved speed of key mapping (fixed errors). * Write block 0 of some gen2 tags more reliable. * Added more well known keys to the extended key file. (extended-std.keys file.
- MIFARE Classic Tool - Donate. IKARUS Projects Tools. Everyone. 66. Add to Wishlist. $5.99 Buy. This is exactly the same version of MIFARE Classic Tool (MCT) as the free one! (Except it will not show the donate notice at startup/updates.) If you like MCT and want to support the developer, please consider to buy this app
GitHub - xavave/Mifare-Windows-Tool: Mifare windows too
Datasheet MIFARE Classic 1k. NFC Forum Type MIFARE Classic Tag. There is an unofficial mapping to store NDEF content to make a MIFARE Classic kind of NFC Forum Tag compliant. cf AN1304 and AN1305. Most NFC-compliant devices recognize MIFARE Classic -based Tags but support cannot be guarantee for all NFC devices Drag and Drop NFC Tools App to your Apps folder; Connect your NFC reader to your computer; Launch NFC Tools For Desktop; On Linux. Download the App image (.AppImage) Set the execution rights : chmod +x nfctools-lastest.AppImage; Connect your NFC reader to your computer; Open the app (./nfctoolsgui.AppImage) Additional informations for Linux Cracking MIFARE Classic. To decrypt the contents of a MIFARE Classic card, we must first find the keys. This will be done in two steps. Find the first key using mfcuk. Now, here is the tricky part. libnfc 1.5.1 must use pcsclite to be able to communicate with the reader, while newer versions of libnfc seem to prefer not to use pcsclite at all. To emulate a mifare card, you need an application running on your smartphone to simulate the phone as a Mifare Classic card. It makes your phone with no difference as a Mifare Classic card. So it can be used with AVEA's MF-WEB08
Tools MIFAR
This is a revolutionary product for MIFARE ® 13,5MHz Card programming. uFR Card Formatter is a programming tool for multiple MIFARE ® card and reader authentication methods by setting various Keys and Key index, linear read and write of the sectors and blocks, defining the sector trailer, files creation and import, and so on MIFARE Classic Tool - MCT 2.1.0 APK Download and save the apk file to your Android Phone's SD card and install it Mifare DarkSide Key Recovery Tool BIBLIOGRPAHY (no specific order) -----Rossum, Roel Verdult, Para la tarjeta se ha utilizado una Mifare classic 4k. Hi! so i was trying to use a chinese card with my proxmark, and it won't an classic terminal: Use the *.mdf fiel you made in Step 1.
MIFARE Classic Tool - Downloa
Crack Mifare card key using brute-force attack with NFC smartphone and Mifare Classic Tool(Modified demystify the security of MifareClassic cards showing how easy is dump, modify and rewrite the content of the card (also clone the card contents utilizing UID writable cards) after discover its keys utilizing cryptographic attacks released to public since 2007. This talk isn't pretend incentive frauds or criminal activities. The author isn't responsible by the use of the presented. This design demonstrates MIFARE Classic authentication on the widely available TRF7970AEVM. Features . Features TRF7970A reader firmware demonstrating authentication of MIFARE Classic Tags ; Allows users to easily change the MIFARE Classic keys used for authentication ; Developed on an easy to use and widely available reference platform, the TRF7970AEVM; Firmware is portable to other. Next we'll take a look at a card that is a little more complicated but ultimately broken, the MIFARE Classic. MIFARE Classic. The MIFARE Classic is a very popular RFID card that's in many different operations like bus fare cards, laundry cards, or ID cards. They're very widespread and unfortunately, very broken. We're going to use the high. Keyboard Wedge - With the keyboard wedge functionality, users of OMNIKEY 5x27 CK readers can retrieve data from a card that is presented to the reader and directly input the card data into an application using keystroke emulation. This eliminates the need for customers to manually enter the card data into an application on a Windows PC. Some copier manufactures of MFD's do support this mode
mifare classic card recovery tools beta v0.1, mifare classic card recovery tools beta v0.1 download, mifare classic card recovery tools beta, mifare classic card. .Sector 0 can be repeatedly rewritable. Mifare clone 1K can be applied to entrance guard system,hotel locks,staff attendance,school campus access, payment control, identification,security systems, parking lot entry and payment, social security management,transportation payment, municipal and ancillary service payment
How to copy MIFARE® Classic Sectors - YouTub
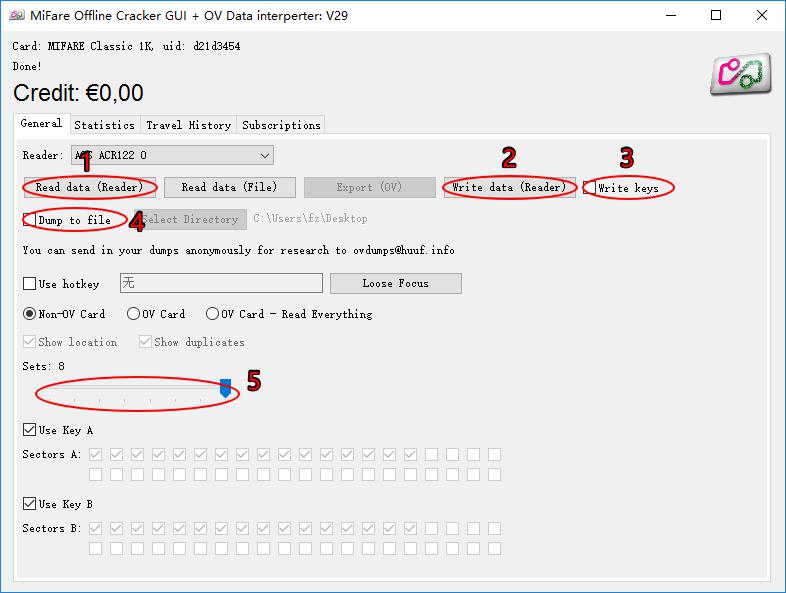
Mifare Classic Offline Cracker Free
Note that it is not related to nfc-tools or this website! mfterm is a terminal interface for working with Mifare Classic tags, written by Anders Sundman. NFCProxy is a an Android app that lets you proxy transactions, written by Eddie Lee. They talk about libnfc/nfc-tools. Poking around on a Mifare card: LibNFC crash course on mcbridematt's blo The MiFare RFID hack, writes Geeta Dayal, used a few tools not in the arsenal of your average code-duffer. But now that researchers have done the heavy lifting, subsequent cracks will be much. Pour écrire sur un tag vierge avec Mifare Classic Tool il suffit d'utiliser std.keys qui contient les clés de base, généralement c'est 12 xF (FFFFFFFFFFFF). Avant tout il faut toujours aller dans Show Options et cocher use these Access Conditions for all sectors : 08778F. Sans ça vous allez écrire des ACs qui vous empêcheront de réécrire certains blocs lors du restore d'un dump exi
This product is not recommended for new designs. Instead, we recommend to use our MIFARE ® DESFire ® Light IC.. NXP ® has developed the MIFARE ® MF1ICS50 to be used in a contactless smart card according to ISO/IEC 14443 Type-A.. The MIFARE MF1ICS50 IC is used in applications like public transport ticketing where major cities have adopted MIFARE as their e-ticketing solution of choice WO2 - MIFARE® Plus EV2: This session consolidates the technical concepts delivered in MO2. It shows how to upgrade MIFARE Plus EV2 to the different higher security levels, both at the sector and card level, and illustrates how to authenticate and perform common memory operations. For this practical exercise, NXP RFIDDiscover and NXP Pegoda Reader (MFEV710) evaluation tools are used The Samsung TecTile NFC tag stickers use MIFARE Classic chips. This means only devices with an NXP NFC controller chip can read or write these tags. At the moment BlackBerry phones, the Nokia Lumia 610 (August 2012), the Google Nexus 4, Google Nexus 7 LTE and Nexus 10 (October 2013) can't read/write TecTile stickers.. MIFARE Classic encryption has been compromised; see below for details MIFARE Classic Tool - MCT is a very popular Android Tools app. It is developed by IKARUS Projects and published to Google's PlayStore and Apple's AppStore. MIFARE Classic Tool - MCT has got a very good number of installations around 500,000+ with 4.0 out of 5 average user rating. MIFARE Classic Tool - MCT for Android
How to use a dump file with NFC on MIFARE classic tool. Close. 3. Posted by 4 hours ago. How to use a dump file with NFC on MIFARE classic tool. It seems the app only allows to read/write NFC tags and I can't figure out how to use the tag with my phone, I've looked everywhere on the internet and couldn't find anything for such a simple task. For example I read and saved my keypass for entering. The MIFARE Classic and MIFARE Plus tag products (see [MF1K, MF4K, MFPLUS]) are ICs enabling a contactless card/tag and are currently available with 1Kbyte, 2Kbyte and 4Kbyte of EEPROM memory. The MIFARE Classic and MIFARE Plus support file data transfer in 106 kbit/s, mutual three pass authentication, data encryption of RF-channel with replay attack protection, and an encrypted data link for. Can the MCT App (Mifare Classic Tool) be used to clone gen1 Mifare Classic cards? Close • Posted by 2 minutes ago. Can the MCT App (Mifare Classic Tool) be used to clone gen1 Mifare Classic cards? From reading, it looked like the app would only work with gen2, but most of the resources I'm finding are out of date... I have a Pixel 4, a Mifare Classic card I'd like to clone, and am hoping to. Download Mifare Classic Tool - MCT app for Android. Read, write, analyze, etc. MIFARE® Classic RFID-Tags!. Virus Fre Can't clone card using MCT Mifare Classic Tool Android - BCC of Block 0 is not valid. Close. 1. Posted by 1 year ago. Archived. Can't clone card using MCT Mifare Classic Tool Android - BCC of Block 0 is not valid. I'm trying to copy my own lift access card because the building I'm in charges 60 USD for a replacement! Its a MiFare Classic 1024byte, (4 byte). I now have the right tags.
Der MIFARE Plus SE ist ein Einsteigerprodukt, das als Ersatz für den MIFARE Classic mit 1K Speicher gehandelt wird, jedoch mehr Sicherheit durch die Unterstützung von AES mit sich bringt. MIFARE Plus EV2 Der MIFARE Plus EV2 verfügt über ein Security Level Konzept, das ein Upgrade von älteren Infrastrukturen zu mehr Sicherheit ermöglicht. Unterstützt Funktionen wie bspw. Transaction MAC. Download Mifare Desfire Tool app for Android. Access MIFARE® DESFire® EV1 NFC smart cards. Virus Fre
NDEF reader/writer tool for Windows, Mac and Linux Desktop PCs for NXP NFC ICs. Similar to NXP's TagWriter App for Android the new TagXplorer tool for PCs allows to read, analyze and write NDEF messages to NXP's NFC tag and smart sensor ICs. The tool is designed using NXP's TapLinx open Java API and it allows the user to perform NDEF. MIFARE Classic ICs started a revolution in the contactless smart card business back in 1994. Today, they're still used in a variety of applications worldwide. The MIFARE Classic EV1 represents the highest evolution of the product family and succeeds in all previous versions. These solutions provide excellent ESD robustness for easy handling of the IC during inlay and card manufacturing and.
Should a Visa Card be using Mifare Classic 1K. Scanning the cards in my wallet with MCT this week, I found that one of my Visa Credit Cards was using Mifare Classic 1K, with the data able to be read with the MCT tool among others. I tried to let my bank know, and this is the response I was given: we simply don't have anyone available to have a specific conversation regarding some of the. #r directive can be used in F# Interactive, C# scripting and .NET Interactive. Copy this into the interactive tool or source code of the script to reference the package Older versions of Mifare Classic Tool - MCT It's not uncommon for the latest version of an app to cause problems when installed on older smartphones. Sometimes newer versions of apps may not work with your device due to system incompatibilities. Until the app developer has fixed the problem, try using an older version of the app. If you need a. This is (ELECHOUSE Proxmark3) how to crack Mifare classic tags by elechouse on Vimeo, the home for high quality videos and the people who love them
If you want to MAKE image (dump) file, you have to have a .mfd file, where keys to all sectors are stored (use Nethemba's MFOC, or the MFCUK utility to get those and create keys.mfd file) dump.mfd is the output file, where the output will be stored (when using with the 'r' option) So you need to type something lik The mifare Classic is the most widely used contactless smart card in the market. Its design and implementation details are kept secret by its manufacturer. This paper studies the architecture of the card and the communication protocol between card and reader. Then it gives a practical, low-cost, attack that recovers secret information from the memory of the card. Due to a weakness in the.
Mifare Classic Tool. Posted on by ikarus › Forums › Apps › Mifare Classic Tool. This topic contains 2 replies, has 2 voices, and was last updated by ikarus 2 years, 1 month ago. Viewing 3 posts - 1 through 3 (of 3 total) Author. Posts March 23, 2015 at 11:04 pm #15135. ikarus. Member. Hi, I recently changed the code structure to be compliant to Android Studio. The new release of MCT (2.0. What Is The Difference Between MIFARE Card & RFID Card A Radio Frequency Identification ( RFID ) device serves the same purpose as a barcode or magnetic strip on the back of a credit card or ATM card NFC Tools Alternatives. NFC Tools is described as 'app which allows you to read, write and program tasks on your NFC tags and other RFID compatible chips' and is an app in the News & Books category. There are more than 10 alternatives to NFC Tools for a variety of platforms, including Windows, Android, iPhone, iPad and Linux
This program allow to recover authentication keys from MIFARE Classic card. Please note MFOC is able to recover keys from target only if it has a known key: default one (hardcoded in MFOC) or custom one (user provided using command line) **** OnePlus One's hardware is compatible with MIFARE Classic®. However, it must be updated to the last version of OmniROM/LineageOS. The word Format means that the NFC Tag must be formatted in NDEF format, in order to be read by this model. NDEF (NFC Data Exchange Format) formatting can be performed with various devices, but not with a smartphone. All the NTAG® chips can be read and. To make things even easier, we added sample code for Mifare Classic cards to our SDK. With that sample code you can load keys to your reader, authenticate under those keys and access Mifare data blocks. With the access conditions satisfied you can reading and writing any card data. We have prepared sample code to demonstrate this. and wrapped it in HelloWorld-style sample code. I've also done a lot of tidying up of the Mifare key handling code (the KeyA and KeyB stuff was probably some of the earliest code I wrote on this project, and was pretty broken!), as I'm starting to see a lot of live security issues with Mifare cards and their use in applications such as hotel keys etc., so I've added copy/clone functionality to readmifaresimple.py (note that it's not capable. Mifare classic can be completely cloned. You can buy cards with changeable UID as well - I just ordered a bunch. The blocks of the card which require non-default keys can be cracked on a PC using cheap hardware. E.g.: Proxmark or Adafruit PN532 / Elechouse PN532 V3, using libnfc and a few other programs. All the tools needed come stock in Kali. But even then, original NXP Mifare Classic cards can't be cloned. While all sectors (including 0) are cloned ok, the clone still behaves differently compared to the original. For example, it reports an SAK of 08, while the clone reports 88 (because 88 is in sector 0). Any modern reader will be able to tell that the card is cloned, so don't bother